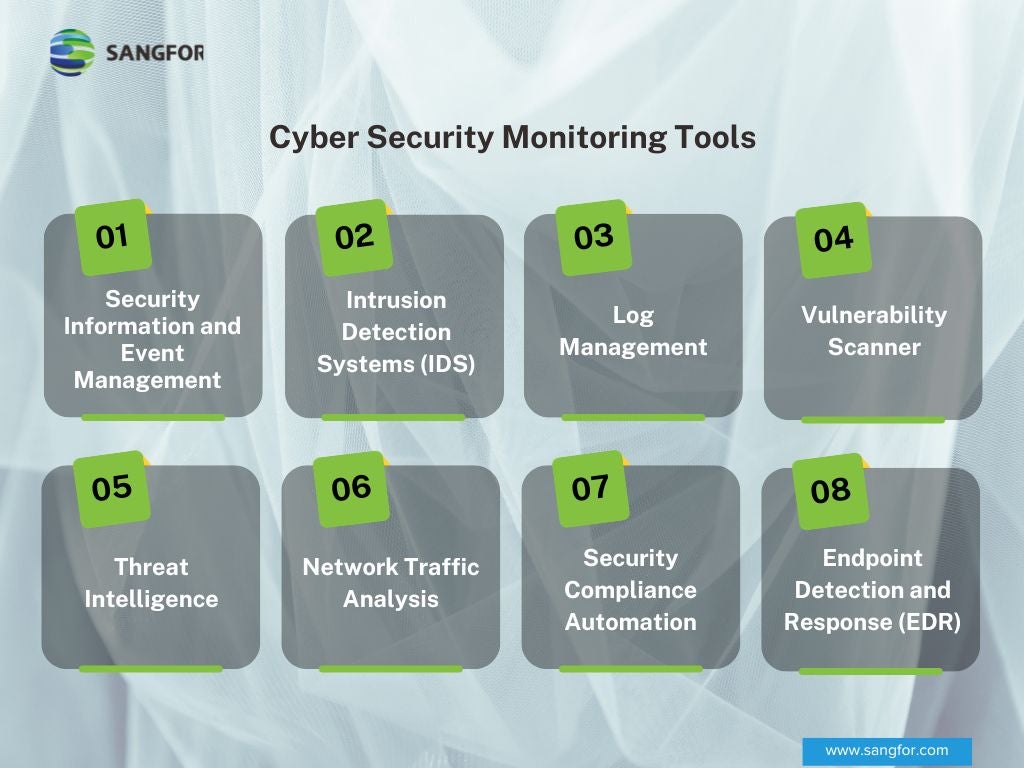
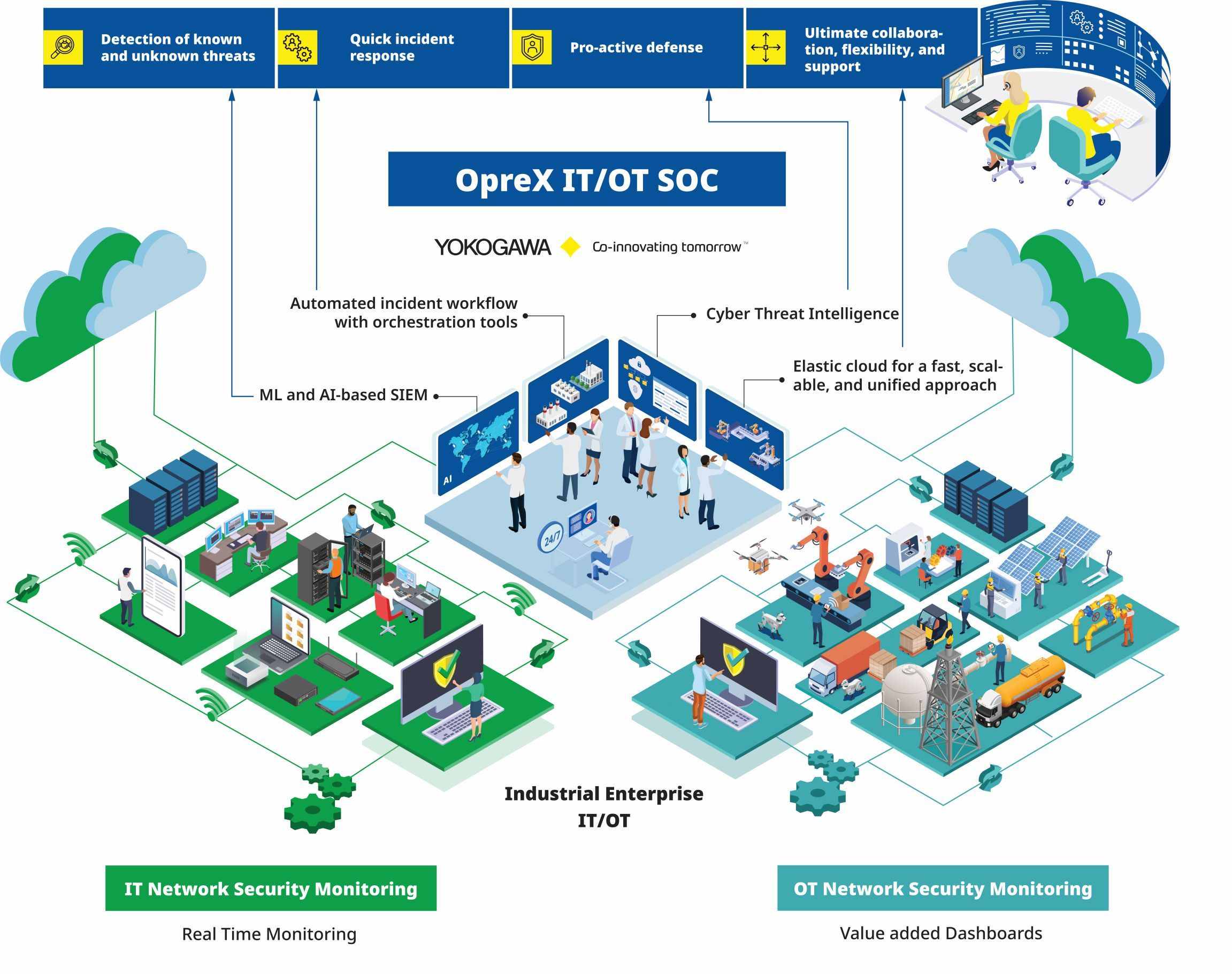
Effective Security Monitoring Plan Cybersecurity Monitoring Implemented Ppt Example | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

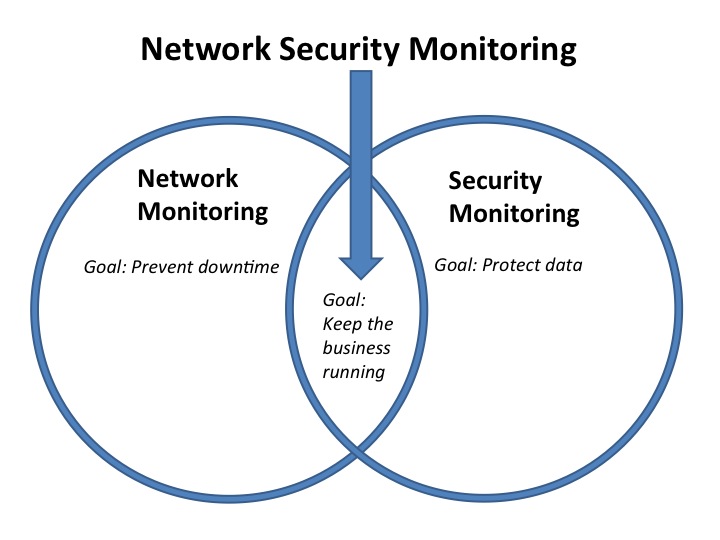
Sensors | Free Full-Text | A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review